THE BEST SECURITY IS A PROACTIVE SECURITY
COMPLIANCE CONSULTING
We help you comply with your prevailing regulatory requirements, respond to situations of noncompliance, and improve your processes around information systems supporting GRC.

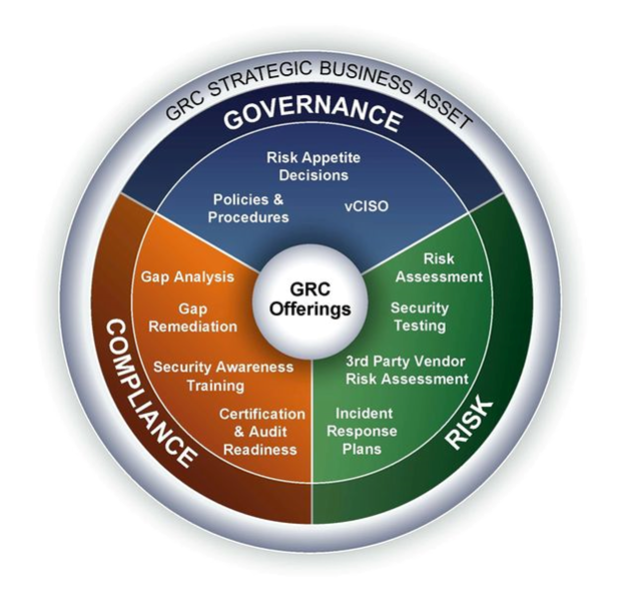
Take advantage of our risk, compliance and security service to understand and manage your risk, achieve and maintain compliance, make certain everyone is trained to spot and avoid a cyber-attack, monitor vulnerabilities, and Dark Web analysis. Form an defensive line of prevention that stops an attack before it strikes.
Our Services Include:
- Risk Assessments
- Technical Assessment
- Vulnerability Assessment
- Penetration Testing
- Simulated Phishing
- Remediation Recommendations and Plans
- Employee Training
- Policy Management
- Risk Management
- Incident Reporting
- Dark Web Monitoring
- Web AD Integration
Your Compliance Road Map
Navigating the Evolution of Compliance Regulations
From NIST, CMMC, HIPAA to PCI to GDPR, compliance regulations are constantly evolving. Cyber Insurance Companies are requesting more and more security controls be deployed before they provide their coverage for your business. Premiums are increasing. All this, and the continuously increasing threats not only from hackers but also from ransomware and malicious external/internal actors put your business at risk. A comprehensive, integrated approach to compliance and minimization of overall business risk – including those of your 3rd party vendors – reduces the possibility of fines, security breaches and negative operational consequences.
PHASE 1
Understand Your Regulatory Compliance

Understanding
Start with the most important question – what regulatory compliance standards do you need to comply with? Every industry is different.
- Besides HR and PII for your staff what other compliance standards do you have to adhere to? GDPR?
- What states do your clients reside in and where do you do business? Are you aware of the different PII and data privacy requirements in each state?
- Do you understand the industry-specific requirements for your business: Healthcare (HIPAA), credit card transactions (PCI-DSS), government business (NIST or CMMC), to name but three.
PHASE 2
Create a Compliance Plan
Discovery
Start with the basics – get a clear picture of who and what is involved with compliance.
- Secure executive ownership – accountability now rests with the Board
- Conduct a thorough asset inventory including data stores
- Complete a compliance inventory to determine which assets are subject to regulations
- Create a map detailing where requirements overlap and efficiencies can be gained
- Identify all departments and stakeholders that share responsibility for compliance
- Create/update the risk register
PHASE 3
Identify Existing Gaps
Assessment
Identify all existing gaps you may have in the areas of people, process and technology:
- Engage your internal Compliance Team or Stealth-ISS Compliance Team
- What data is in scope for regulatory requirements? Minimize scope, reduce cost
- How is that data obtained, processed, archived and deleted?
- Identify all regulatory compliance gaps
- Remediate areas based on people, process, technology
- Create implementation plan and timelines

PHASE 4
Put Your Planning in Motion

Pre - and During Implementation
Put your plan in motion. Be sure that all involved diligently adhere to governance rules.
- If needed, engage experts/consultants in the process, build a plan
- Establish a centralized compliance committee
- Clearly explain that compliance does not automatically equal security
- Create a separate security protocol – third party or fractional CISO/Compliance officer – including third-party vendor policies
- Establish compliance parameters and conduct employee training
- Implement all remediation efforts identified during Phase 3
PHASE 5
Maintenance and Operations
Ongoing Maintenance
- Compliance isn’t static; regulations change. We make sure your organization stays current:
- As you change your business operations (expand and grow, implement new technologies, bring in new vendors and partners)
- Ensure new IT solutions and business operations support compliance at the organizational and departmental levels
- Leverage analytics to identify gaps or red flags
- Refresh employee training on a yearly basis and stay on top of new regulations
- Create a compliance strategy, manage risks and perform assessment to make sure controls met
