PENETRATION TESTING SIMULATION
OPTIMIZE THE EFFECTIVENESS OF YOUR SECURITY CONTOLS
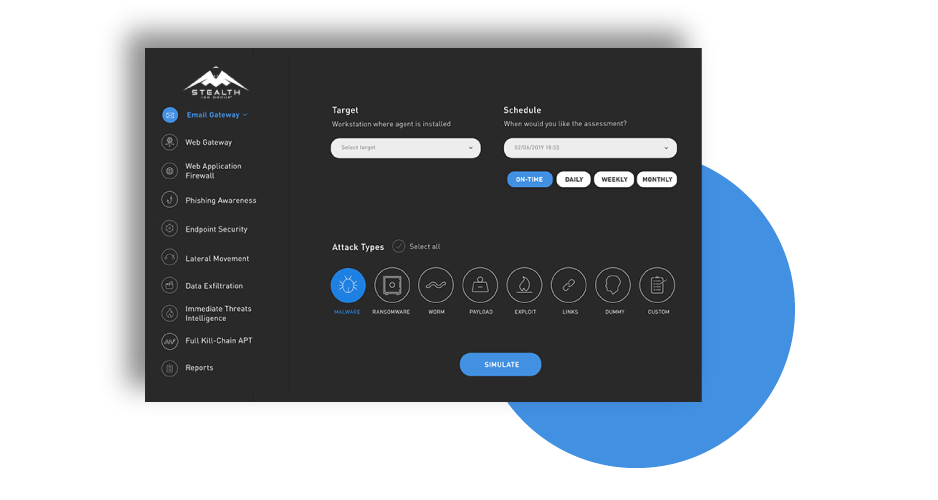
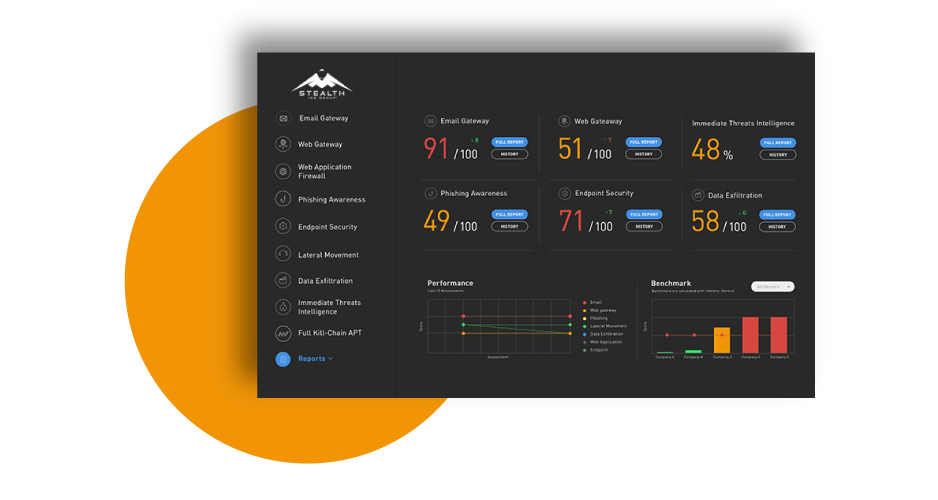
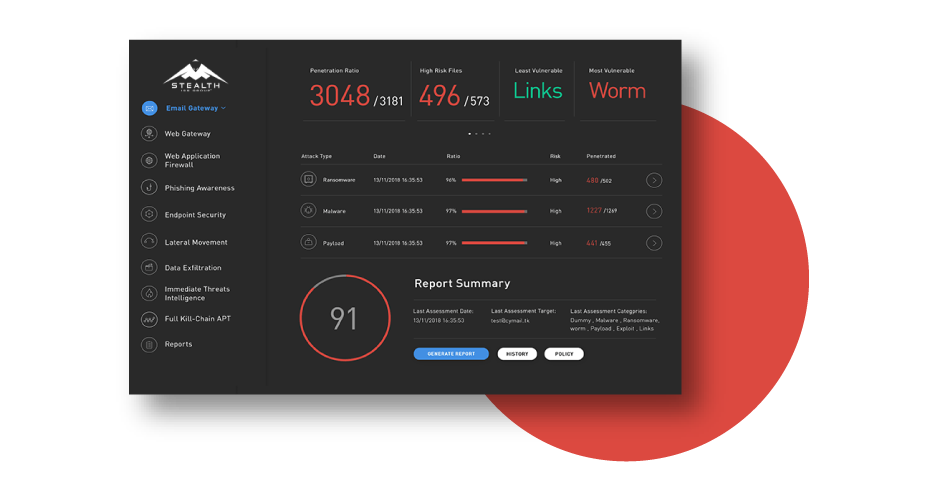
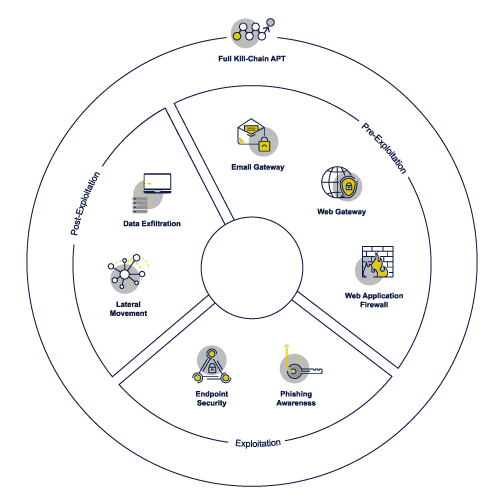
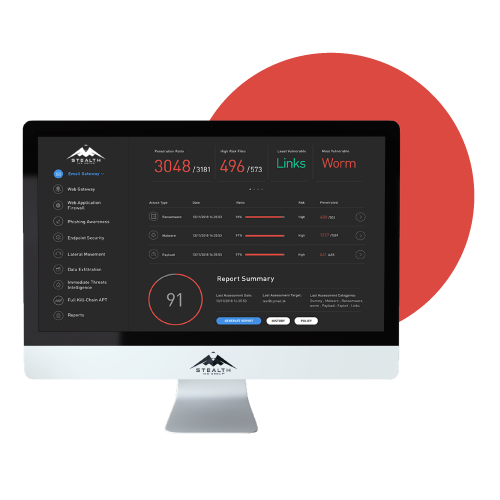
We validate and manage your security posture in three simple steps with an automated SaaS-based breach and attack simulation platform – it’s as simple as a click of a button.