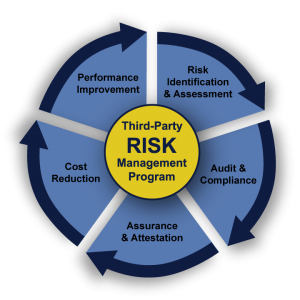
Our Methodology includes:
- Partner Trust Assessment (definition of Security Requirements using a Risk Based Measure)
- Privacy Impact Assessment (measures Privacy and Data Governance Controls)
- Business Impact Analysis (a measure of impact to your business given an unavailable service)
- Classification of partner risk level, and creating custom security requirements
- Testing and assessment to ensure third party security requirements are in place
- Follow-up activities with your team and your Vendor or Partner to ensure issues are remediated