VULNERABILITY SCANNING
WE IDENTIFY THE VULNERABILITIES WITHIN YOUR NETWORK TO HELP PROTECT YOUR CRITICAL ASSETS AND STAY AHEAD OF CYBERATTACKS.
PROTECTING YOUR CRITICAL ASSETS WITH MANAGED VULNERABILITY SCANNING
Technology is advancing. Regulatory requirements are changing. The cybersecurity skill gap is growing. These challenges make managing today’s threats increasingly difficult. If you are not equipped to handle the pace of today’s threats, then your overwhelmed team may have to scramble to avoid the costly fines of noncompliance.
Managed Vulnerability Scanning relieves the time consuming, costly, and stressful burden of vulnerability identification. In return, you are able to free up your resources and focus on the business objectives that matter most to you.
EXPLORE OUR CAPABILITIES
Network Scanning
To protect your network, we scan your IP address ranges to discover open ports and other security vulnerabilities specific to your network devices.
Dynamic Assets Scanning
We scan your assets for vulnerabilities with unsurpassed accuracy-even highly dynamic IT assets like IoT devices, virtual machines and cloud instances.
Cloud Visibility
In order for you to achieve continuous visibility, we can scan your public cloud environments scan as Amazon Web Services, Microsoft Azure and Google Cloud Platform.
HOW WE KEEP YOUR NETWORK AND APPLICATIONS SAFE
VISIBILITY INTO YOUR NETWORK
- We automatically discover all the elements of your network: computers, laptops, mobile phones, tablets, printers, servers, virtual machines, routers, and switches.
- We group your devices for better management. You are able to distribute management to different teams and still see everything from one central management dashboard.
WE FIND THE GAPS
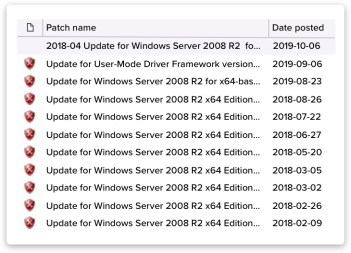
- We scan your network for missing patches. Over 5,000 patches are released every year, meaning that any one may be the flaw that hackers target. This is where hackers start.
- We find the gaps in Microsoft, MacOS, and Linux operating systems. We identify missing patches in web browsers and third-party software, such as Adobe, Java, and 60 more major vendors.
- We identify non-patch vulnerabilities with an updating list of 60,000+ known issues, as well as items like open ports, system information about users, shared directories, and services.
HOW WE KEEP YOUR NETWORK AND APPLICATIONS SAFE
- We send you reports on compliance and vulnerability fixes.
- Compliance regulations have many requirements to ensure financial, health, or other personal data is secure in networks and systems. Failing to comply or demonstrate compliance can mean serious fines, angry customers and lost business.
- Get the reports auditors need to demonstrate compliance for the multiple requirements in PCI DSS, HIPAA, SOX, GLBA, PSN, and CoCo regulations.