24 HOURS TO FULL CAPABILITIES
SOC-AS-A-SERVICE (XDR)
We utilize leading technology to support our SOC-as-a-Service offering. Two clicks is all it takes to get Stealth-ISS’s agents auto-installed across all endpoints. Compliant with PCI, HIPAA, and GDPR regulatory requirements.
DO YOU WANT TO PROTECT YOUR BUSINESS, DATA, AND MEET COMPLIANCE REQUIREMENTS?
ARE YOU LOOKING FOR A TRUSTED MSSP WITH THE TOOLS AND KNOW-HOW TO MONITOR YOUR IT ENVIRONMENT 24/7?
DO YOU WANT PROTECTION FROM INTERNAL AND EXTERNAL THREATS, MALWARE, PHISHING, RANSOMWARE, AND THE PEOPLE BEHIND IT?
YOUR 24/7 SOC-AS-A-SERVICE
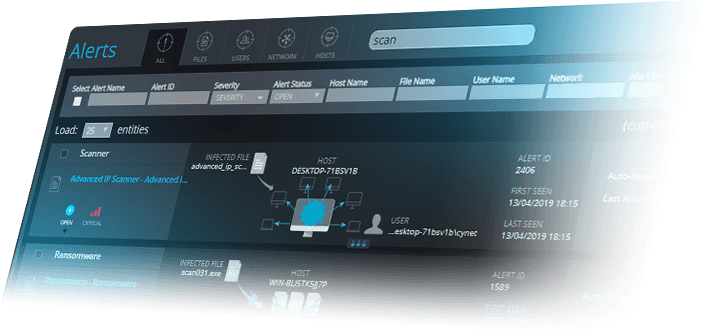
MONITORING & CONTROL
- Getting integrated visibility to all that takes place in the environment, typically entails manual aggregation of various different log feeds, making this critical need for IT Security teams unaddressed.
- Our SOC-as-a-Service offering provides you with visibility in all endpoint configurations, installed software, process execution, network traffic and user activity, enabling operators to optimize their asset management and proactively reduce exposed attack surfaces.
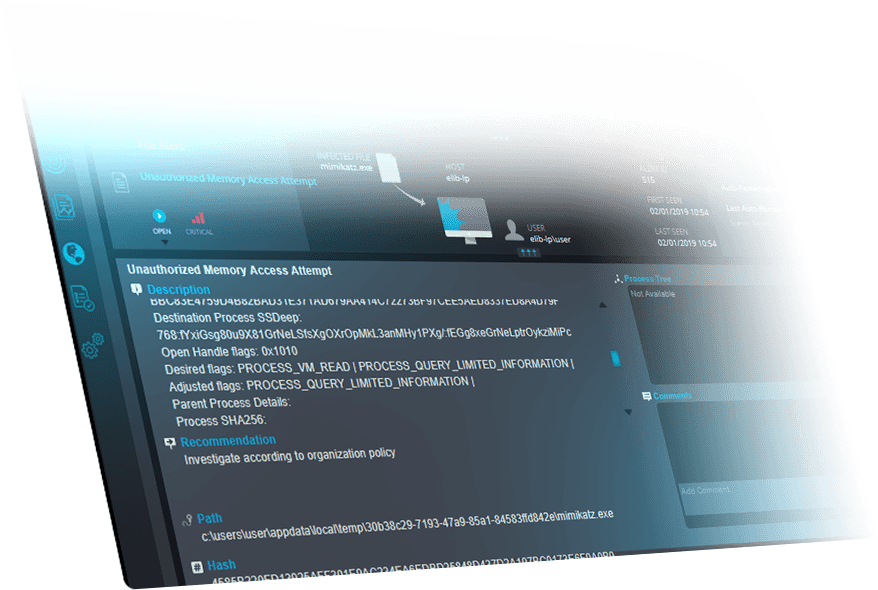
NEXT-GEN ANTIVIRUS PROTECTION

Threat Intelligence
We utilize over 30 live feeds of various Indicators of Compromise.

Known Malware
We identify and prevent execution of malware with known signatures.

Fuzzy Hashing
We identify files with high similarity to know malware hashes.

Memory Access Control
We ensure only legitimate process can gain access to critical areas in memory.

AI Static Analysis
We analyze files before execution using unsupervised machine learning to discover malicious attributes.

Behavioral Analysis
We monitor process at runtime and terminate upon detection of malicious behavior.
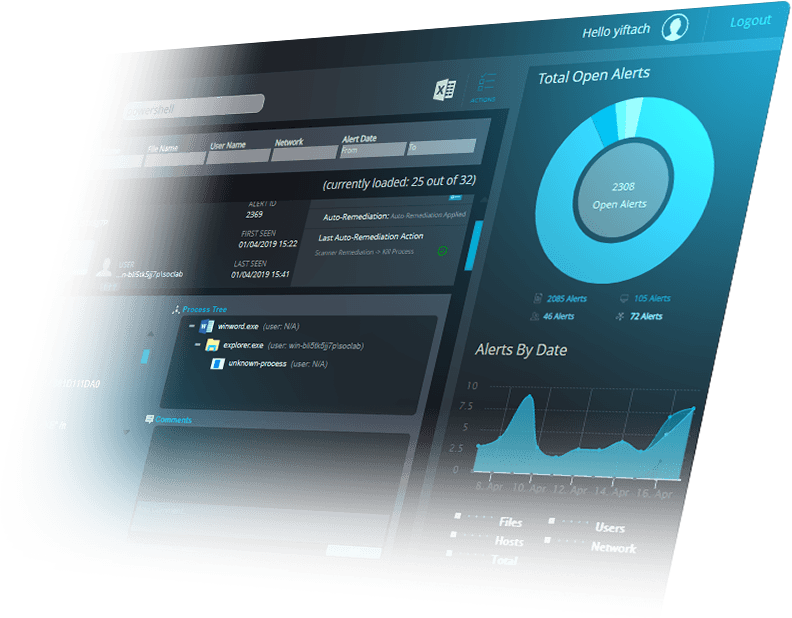
ENDPOINT DETECTION & RESPONSE
Today’s attackers can easily bypass your preventative measures and utilize tools to operate under the radar.
With Stealth-ISS’s SOC-as-a-Service, we continuously monitor your endpoints for active malicious presences in order to make rapid and efficient decisions that eliminate threats.
USER BEHAVIOR ANALYTICS
Stealth-ISS’s SOC-as-a-Service prevents execution of malicious code by enforcing a chain of interlocking protection layers on executed files and running processes.
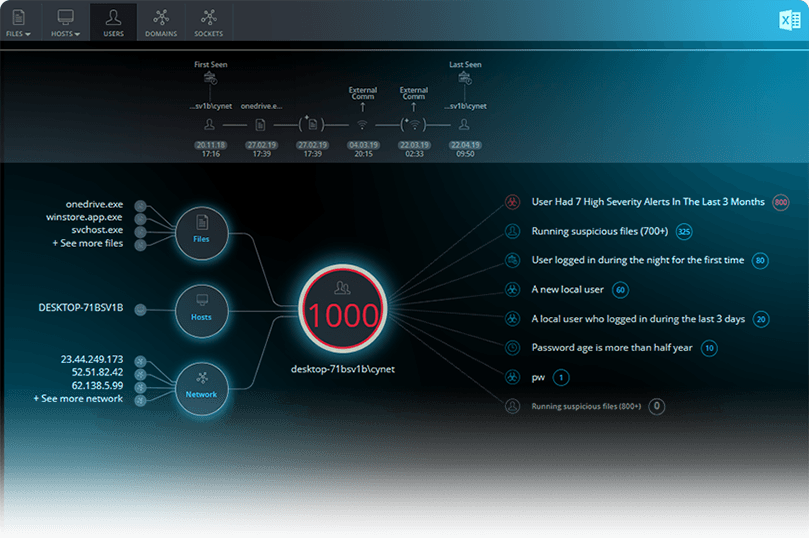
User Behavior Baseline
Stealth-ISS utilizes real-time user activity monitoring to achieve a baseline, utilizing the number of hosts they log into, location, frequency, internal and external network communication, accessed data files and executed processes.

Real-time activity context
Real-time activity context is achieved through continuous correlation of user activities with other entities’ events, including endpoints, files and external network locations, providing you with rich context to determine associated risk.
Enhance Accuracy With User Verification
We leverage internal knowledge of users’ roles, group, geolocation and working hours to define access patterns to SaaS and on-premise resources that are likely to indicate user account compromise.
Examples include first-time logins to resources, logins outside of working hours, logins to multiple machines within a short timeframe, etc.
NETWORK ANALYTICS
Stealth-ISS prevents execution of malicious code by enforcing a chain of interlocking protection layers on executed files and running processes.

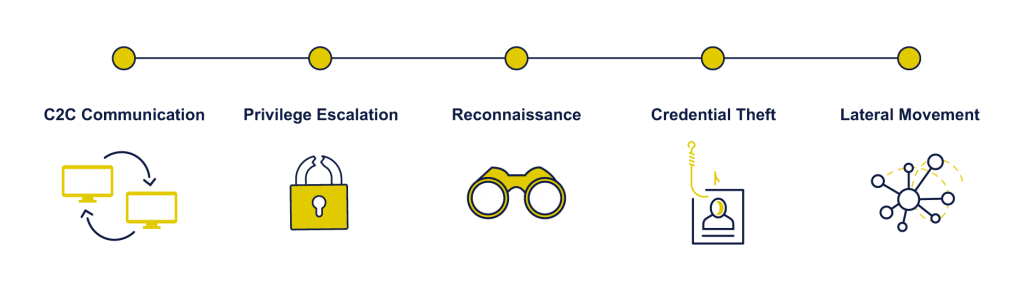
Reconnaissance
Gathering information on the attacked environments is a prerequisite for efficient malicious expansion and is typically executed by any type of port scanning.

Risky Connections
Active communication with malicious sites includes malware distribution, phishing, and known C2C based on intelligence feeds.

Credential Theft
Gaining user account credentials is a key enabler of lateral movement. To obtain these credentials, attackers exploit networking mechanism weaknesses to extract password hashes from intercepted internal traffic.
Lateral Movement
For advanced attackers, the first compromised endpoint is merely a mean, not an end by itself. The attack’s true objective resides on other endpoints or the server. There are numerous vectors to spread across an environment, many of which generate unique network traffic.

Data Exfiltration
The final stage in any attack is to exfiltrate compromised data from the internal environment to the attacker’s premises. A common way to evade perimeter defenses is to disguise the exfiltration as a legitimate protocol, such as DNS, HTTPS, etc.
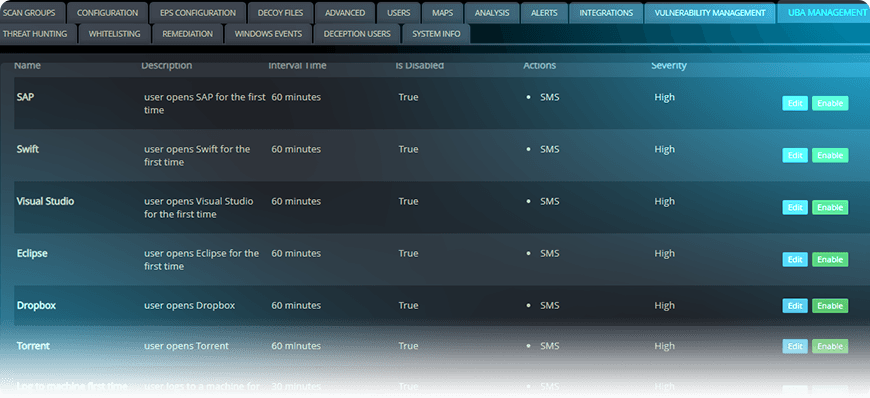
PRE-BUILT REMEDIATION USE CASES
USER
Stealth-ISS detects anomalous login attempt.
Disable the user locally on the host using built-in Disable User remediation.
NETWORK
Stealth-ISS detects a host initiating suspicious traffic to an unknown external address.
USER
Stealth-ISS runs IOC search and discovers a malicious service running on host.
Stealth-ISS enables built-in Delete Service remediation to surgically remove the service without the need to isolate the entire host.
FILE
Stealth-ISS detects a suspicious file running on host.
Remove the file for further investigation using built-in Quarantine File remediation.
MAN IN THE MIDDLE
Stealth-ISS detects a Man in the Middle.
USER
Stealth-ISS investigation reveals live trojan malware running on a host.


